Protected Assets – Energy and Cyber Security
The energy sector has been identified as the sector most targeted for malicious attacks that may compromise cyber security, according to the most recent threat report from the Australian Cyber Security Centre.
How are energy networks and other utilities managing this increasingly prominent risk?
Energy networks are undertaking increasingly intensive risk management in cyber security, which is likely to feature prominently in Board-level risk assessments. The cultural change required for cyber security is akin to the health and safety journey of the 1990s, to ensure it is taken seriously and risk mitigation and threat response measures are not only appropriate but subject to continuous vigilance.
In our rapidly growing digital economy and our online community, managing cyber security is now a core capability. Community outcomes increasingly depend on digital services and advanced communications and the energy system is no exception.
As the traditional energy network model transforms and becomes more complex and interactive, service providers face new cyber hazards to the security of grid assets, management systems and customer data. The reliance on advanced control systems, digital solutions and big data mean utilities must be positioned for a rapid transition, rather than an incremental one.
State of security
The PwC Global State of Information Security® Survey 2017 reported that the number of detected security incidents has fluctuated significantly, rising one year and falling the next. According to the report, in 2016, power and utilities companies detected 24% fewer security incidents than the year before. While sources and sophistication of attacks are evolving, phishing schemes and ransomware remain the most common threats.
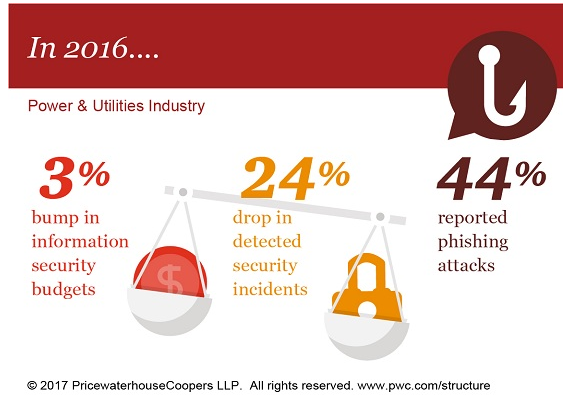
Utilities are improving their ability to detect threats and have increased their information security budgets. In 2016, security spending by international utilities increased by 3% from the year before and expanded 53% since 2012. Similarly, PWC found that information technology budgets of international utilities have increased 62% during the past four years.[1]
Repeated cyber security incidents experienced by energy networks overseas, such as the disablement of large parts of an electricity grid in Ukraine in 2015, have reinforced the potential vulnerability of unprepared network operators.
The sophisticated and malicious cyberattack on the Ukraine grid caused a power grid to be electronically shut down for several hours, impacting approximately 225,000 customers. Systems had been compromised by the use of “spear-phishing” emails – a strategy where fraudulent emails are sent as if from a known or trusted sender to encourage targeted individuals to reveal confidential information. Cyber attackers were able to cripple these systems and delay restoration of grid operations. It illustrated the vulnerability for unprepared businesses and the need for staff awareness of good cyber security practices.
In Australia, the Australian Government’s Australian Cyber Security Centre (ACSC) released the 2016 Threat Report. It identifies that between July 2015 and June 2016, CERT Australia responded to 14,804 cyber security incidents affecting Australian businesses, 418 of which involved systems of national interest (SNI) and critical infrastructure (CI).[2]
Under a voluntary reporting scheme, the energy sector was identified as the sector with the highest number of reported incidents or near-incidents relating to critical infrastructure.
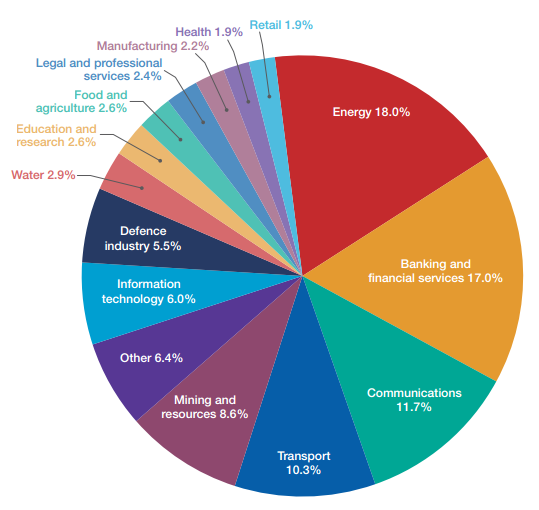
Incidents involving systems of national interest (SNI) and critical infrastructure (CI) by sector. Source:ACSC Threat Report 2016, page 15
Collaborating on security
Energy networks are engaging in ongoing discussion with all stakeholders including the Australian Government, utilising available resources such as CERT Australia and the Attorney-General’s ‘Trusted Information Sharing Network’ (TISN).
CERT is the Australian Government contact point for cyber security issues affecting major Australian businesses, including owners and operators of Australia’s critical infrastructure and other systems of national interest. CERT is a major contributor to the ACSC and provides services such as advice and assistance on how to deal with cyber security incidents, latest information on trends, and participation in company training programs and incident response exercises.
The Australian Signals Directorate (ASD), also a member of the ACSC, provides strategies to mitigate cyber security incidents such as their customisable ‘Essential Eight’ strategies, which are:
- Application whitelisting;
- Patch applications;
- Disable untrusted Microsoft Office macros;
- User application hardening;
- Restrict administrative privileges;
- Patching operating systems;
- Multi-factor authentication; and
- Daily backup of important data.
Internationally, there are other well-documented, mature cyber security frameworks available for use. Australian energy network businesses typically use a combination of the following:
- SANS Institute 20 Critical Controls;
- USA Government National Institute of Standards and Technology (NIST) Cyber Security Framework; and the,
- USA Government Department of Energy Cyber security Capability Maturity Model (C2M2).
Cyber security: the next ‘health and safety’
This significant shift in response to an emerging threat or trend is nothing new, and lessons can be learned from the dramatic increase in focus on occupational health and safety during the 1990s. Health and safety is now an integral part of every business. Senior executive positions are devoted to its management and every employee undertakes preventative training and knows to report near misses and actual incidents.
Businesses have learned from the health and safety journey and are increasing the priority placed on cyber security, requiring engagement within every part of a business and from every employee, contractor and supplier.
Energy network businesses are working to ensure cyber security measures remain appropriate, anticipating and meeting evolving threats. To do this sustainably, the health and safety journey tells us that it requires leadership and resources.
Boards overseeing strategic risk management have adopted a major focus on cyber security with structured approaches to ‘deter, detect and defend’ key risks. Chief Information Officers (CIO) are accountable for regular reporting on information security, much as they would for Health and Safety. Training and awareness of good cyber security practices, such as not connecting unknown USBs or other devices to company computers, is becoming as commonplace as where to locate a fire extinguisher.
Cyber security and Energy Networks Australia
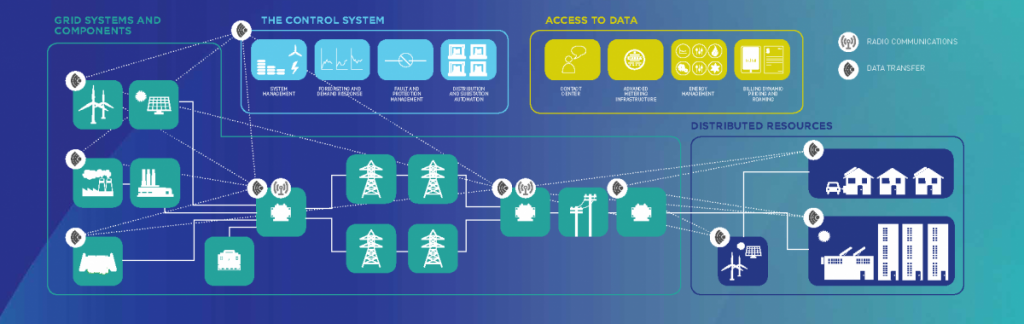
Energy Networks Australia has produced a ‘Cyber Security and Energy Networks’ fact sheet that provides an overview of key dimensions in cyber security relevant to the energy system:
- The grid systems and components relied on by energy networks, including technology providers, individual components or systems they procure;
- The control systems used to monitor and control the network to support energy flows safely and reliably;
- The access to data which safeguards privacy and commercial confidentiality; and,
- The diverse and growing distributed resources that increasingly form a core part of the energy system.
- The risk that cyber intruders may gain a foot hold in Corporate IT systems and Operational Technology (OT) systems like SCADA is well recognized. However, the increased complexity of energy systems creates the potential for a new paradigm.
Transformation and cyber security
Australia’s energy system is experiencing the rapid adoption of distributed energy resources, such as smart meters, smart inverters, electric vehicles, rooftop Solar PV, battery storage and home energy management systems. Many of these technologies are connected through the ‘Internet of Things’ (IoT) and represent a fast evolving relationship of millions of IoT devices with energy networks, where they are not simple ‘loads’ on the system, but providers of energy, demand response or ancillary services. Communication within this ecosystem of IoT devices will be increasingly relied upon by energy networks to play a key role in real-time system balancing and operations supporting the reliability, safety and quality of energy supply.
As a result, a core capability of energy networks must be managing cyber security as devices are integrated. This requires careful management of interfaces, strong communication protocols and setting of safe operating parameters to manage risks to other IoT devices, network components and control systems to ensure continued quality of service delivery.
The US Department of Energy (DOE), in its latest Quadrennial Energy Review (QER) reinforced this point of increasing complexity as electricity provision becomes increasingly interactive between the grid and the customer.
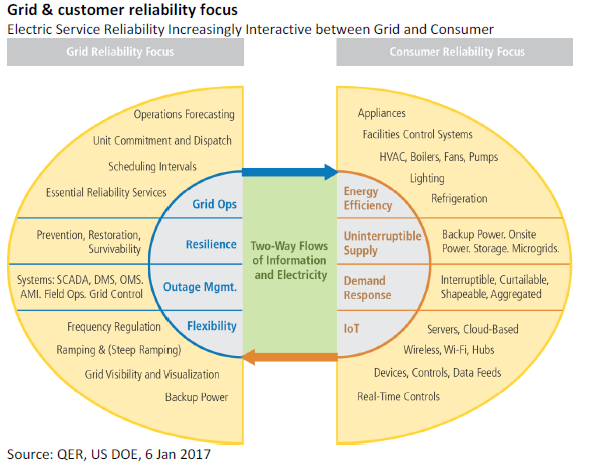
As this complex scenario is realised, two-way flows of information and electricity increasingly places cyber security emphasis on all parts and stakeholders of the power system, including customers and suppliers of DER and other components.
Cyber security is also a core focus of the Electricity Network Transformation Roadmap for the electricity network industry in the coming decade. In a transformed energy system which takes advantage of digital technology and decentralised resources, a strategic focus on cyber security will be an essential priority.
The Roadmap identifies a number of key gaps in standards required to enable the future requirements of the power system. These include key areas such as interoperability, communications frameworks and protocols, control systems and protocols, data frameworks and protocols and cyber security.[3] It proposes an IEC standard on communication networks and cyber security[4] should be reviewed with a view to its application in Australia.[5]
Such standards will work to link in with other elements of cyber security frameworks and enable interoperability of new technologies while ensuring the ongoing cyber security of the grid as it continues to evolve.



